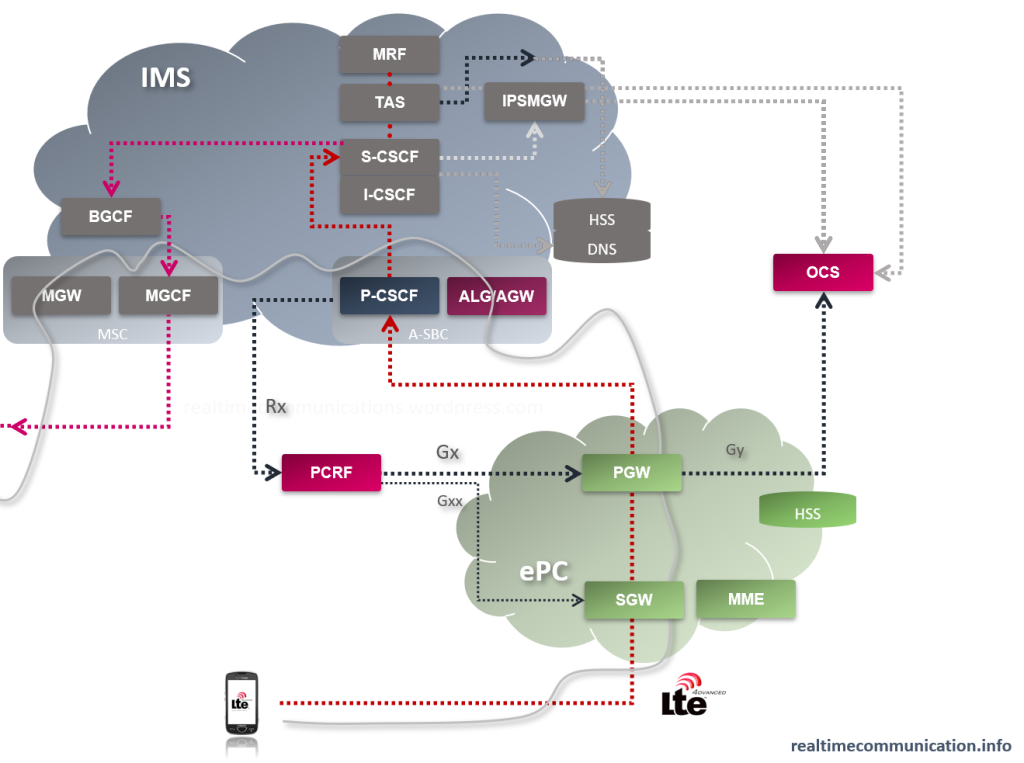
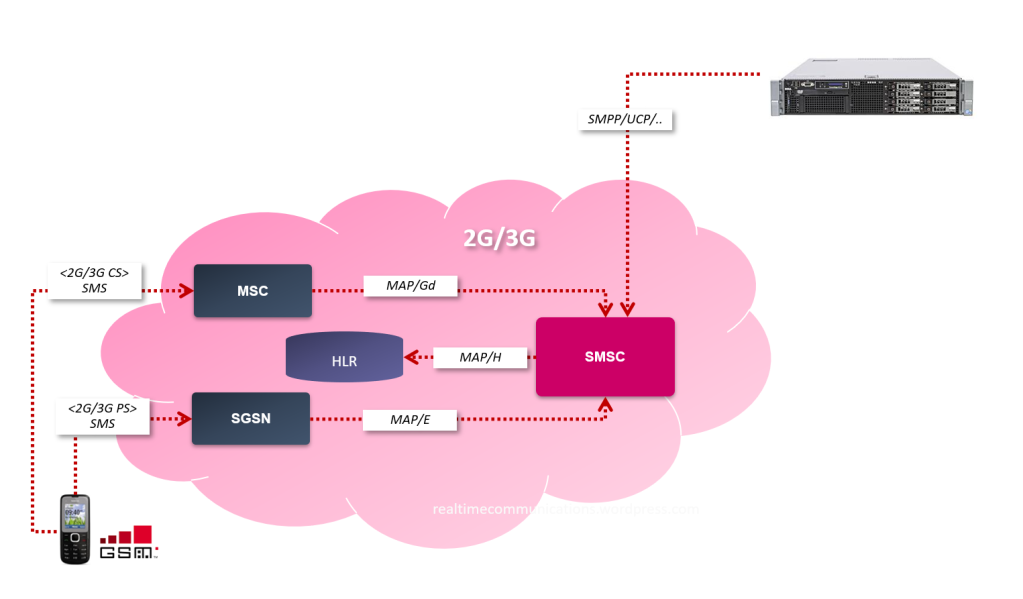
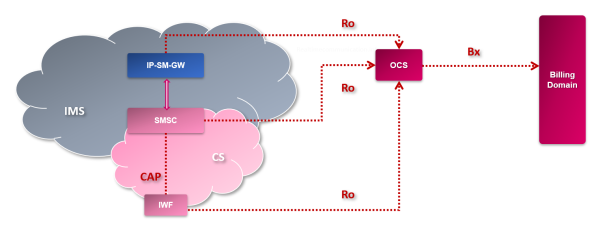
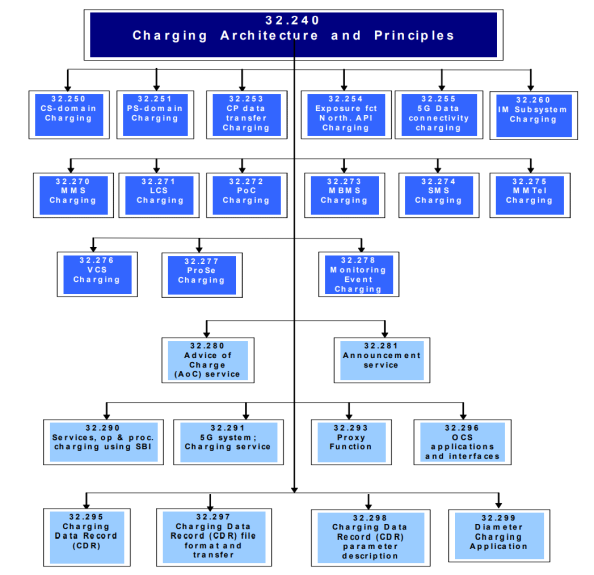
The recent earthquake in Türkiye and Syria reminded everyone how important the disaster and recovery management is. Mobile network was the first part of the critical infrastructure which was involved in the emergency situation. Although it was partially damaged itself, right from the beginning it had to withstand the initial load of calls and further support coordination of AFAD responders, police, gendarmerie, soldiers, volunteers and other personnel. At the same time it had to maintain the regular calls, which were not less important. Mobile communication was helping to reunite families as well as to provide access to important information and news.
The same way everyone should recap first aid procedures time to time, operators should recap the disaster and recovery plans and emergency communication flows. I’m currently working on mobile network deployment in Mexico, where earthquakes are a common place. Therefore we take this very seriously and we know there is no excuse for us if we fail.
Let’s quickly go through the basic requirements on emergency calling in mobile networks.
Continue reading